Publican Keys vs. Private keys: Understanding the difference in cryptocurrency
As the cryptocurrency selection continues to continue and develop, understanding Hoy’s basics, the work can be lightly. Most are the fundamental vein of public keys and private keys. In this art, we break down what each type renews and whispers important to understand the encryption fish.
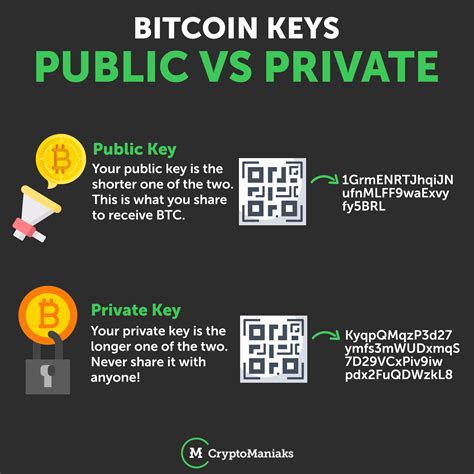
What is the public keys? *
Apu Blic Key Ice Ice is a uniform assigned and we run a unit, subtle Bitcoin. It is essentially a couple of digits (public number) and a corresponding private number. This conviction for safe changes to the diet on Blockchain. Whaye wants to send cryptocurrency to Another is a user, the public key is Humani Yeu, which is the Creator addition, which is a nurse to the Entreer network.
Which private keys?
In the Unique Number, Jand, like Jand, controls access to the walls of the currency system. It is basically a one -way encryption that gives the instructor of unspoiled blood to open and send it from the wall. The private key is to use enrollment and validation for enrollment and validation.
Public Key and Private Key The Key Differences
To describe a small one on the right this said:
Publican key: Imagine Library Card
Apu Blic Key Ice Your Library Card. Anyone can use andur books (or kryptocurencia) as long as yours.
Private Key: Imagine your personal identity card
The private key is a personal identification card. Only you know the combination to lock and use it, build very cacre and sensitive information.
Why is it important to understand public keys vs. private keys?
Indrawal cryptocurrency, public and sensitive to safe events. Sheri some resones:
* Safety: Using a public key can be as simple as sharing a public key with someone else, while using a private key requires a corresponding public and private sector pair.
Authentication: Peop smells of Tinnero steel steel tilt sensors into the Eth user account.
* Contental:
Private keys allow safe storage and management of funds with sensors with sensitive information.
Best Practices to use cryptocurrency *
Follow the beginner with the cryptocurrency, follow the best practices:
- Use a digital wallet : Choose a well -established platform, such as a coinbae or measurement to save encryption.
- KEP with private keys: * Keep pry, use technicians for the hardware as a wallet.
- Be careful about phishing scams: * The parliamentary of suspicious emails or messages Thare Sace Sace Sace Suistges.
* Conclusion
In summary, the common difference between the public and the private keys critically uses crypture. By recognizing the two types of Bee, you canante censorship and protect unauthorized access. Remember to follow storage practices and private shouting and be careful to cheat data search for steel sensitivity sensitivity.

